Netec Power Learning
Online education reimagined for today
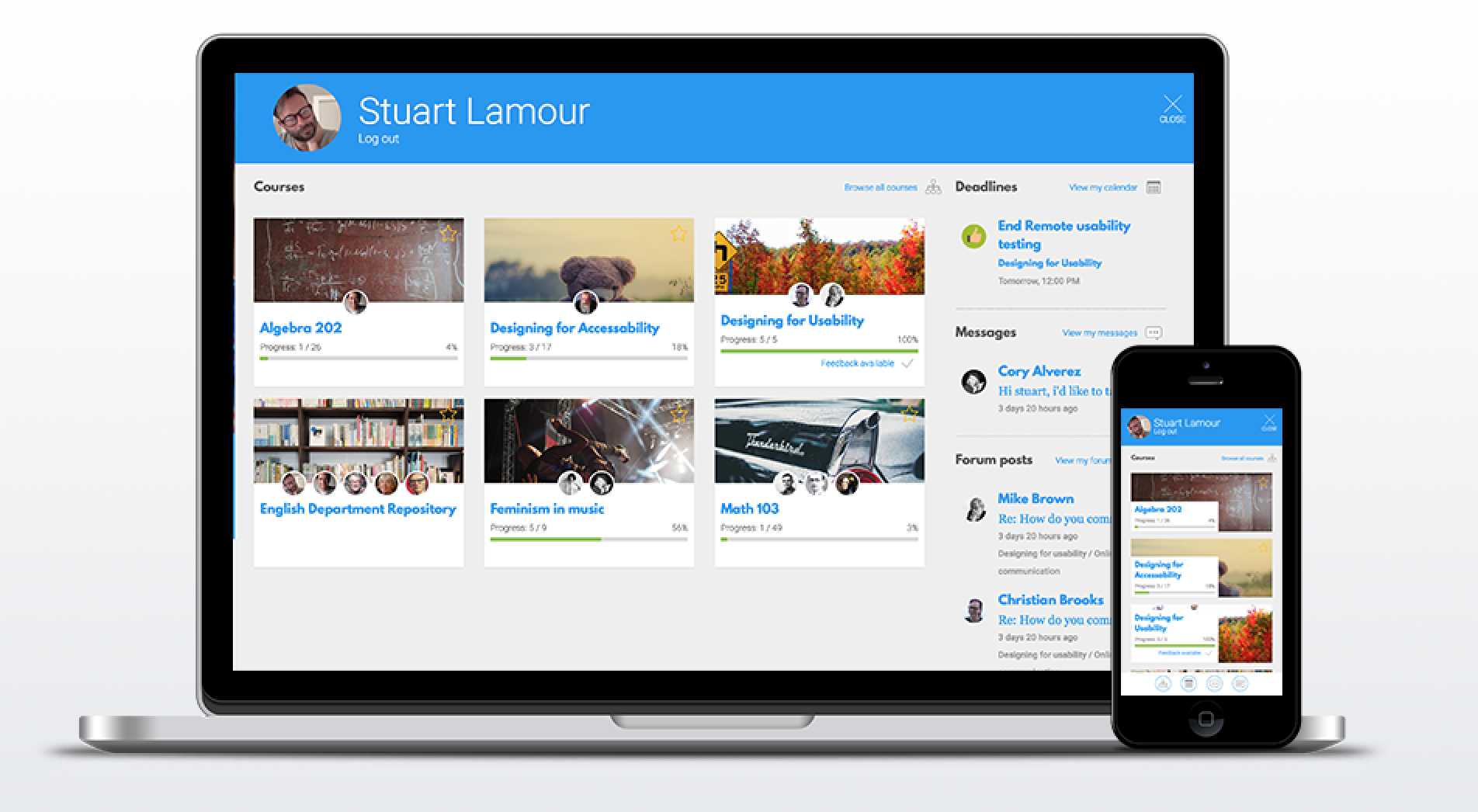
Snap is designed to make e-learning enjoyable-learning for everyone.
Learner Focused

Snap's user centered design makes learning a pleasure, enabling your learners to truly enjoy and get the most out of their online courses.
Educator Focused

Clear intuitive workflows make educators lives easier, so they can happily focus on teaching and not learning to use the LMS.